Ransomware Greatest Risk to Supply Chain in Minds of IT Pros – TechNewsWorld
Ransomware is the top supply chain risk facing organizations today, according to a survey released Monday by ISACA, an association for IT professionals with 140,000 members in 180 countries.
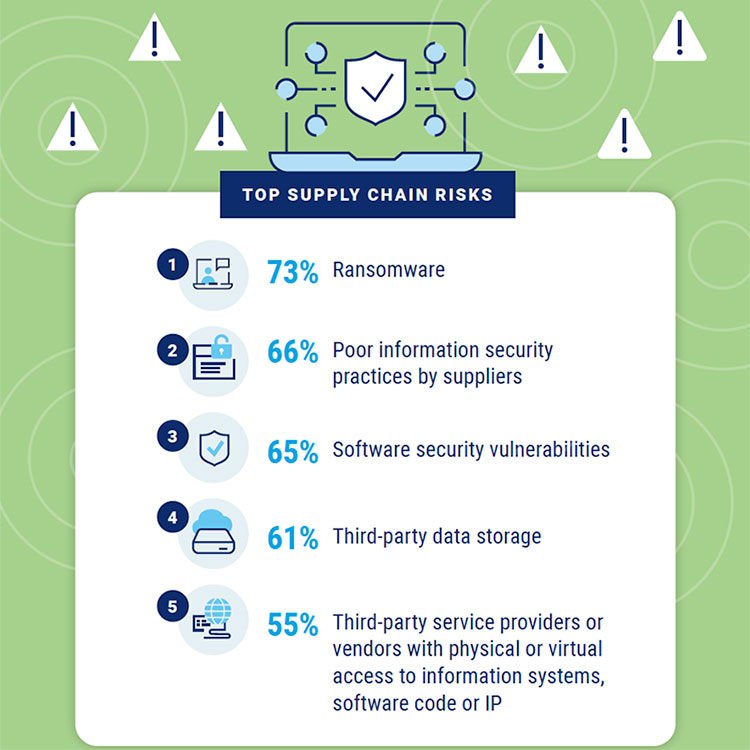
The survey, based on responses from more than 1,300 IT pros with supply chain insights, found that nearly three-quarters of the respondents (73%) said ransomware was a key concern when considering supply chain risks to their organizations.
Other key concerns included poor information security practices by suppliers (66%), software security vulnerabilities (65%), third-party data storage (61%) and third-party service providers or vendors with physical or virtual access to information systems, software code or IP (55%).
The heightened concern over ransomware may be because it can have a double whammy on an organization.
“First, there is the risk of an attacker finding an attack pathway into an organization from a compromised vendor or software dependency, as we saw with the SolarWinds and Kaseya attacks that affected a massive number of downstream victims via that supply chain,” explained Chris Clements, vice president of solutions architecture at Cerberus Sentinel, a cybersecurity consulting and penetration testing company in Scottsdale, Ariz.
“Then there are secondary effects,” he continued, “where a ransomware gang may steal data stored at a third-party provider and attempt to extort both organizations by threatening to publicly release it if a ransom isn’t paid.”
“The other side of the coin is that a ransomware attack on an organization’s supply chain can cause significant operational disruption, if the third party it depends on is unable to provide services due to the cyberattack,” he told TechNewsWorld.
Those attacks on the software supply chain can have a ripple effect on the physical supply chain. “Ransomware contributes to significant disruptions in an already taxed supply chain when systems that manage the manufacture and distribution of goods and services are taken offline,” observed Erich Kron, security awareness advocate for KnowBe4, a security awareness training provider in Clearwater, Fla.
“This can impact ordering and tracking of inventory of the materials needed to make items, impact the status tracking of items needed to fill orders and can create logistical problems getting materials to customers, creating shortages for their customers,” he told TechNewsWorld.
“In a world of just-in-time order fulfillment, any delays can cascade down the supply chain, impacting more and more people along the way,” he added.
Nearly a third of the IT pros surveyed (30%) revealed that the leaders in their organizations did not have a sufficient understanding of supply chain risk. “The fact that it was only 30% was somewhat encouraging,” ISACA Board Director Rob Clyde told TechNewsWorld. “A few years ago that number would have been far higher.”
“I think a lot of the ignorance comes from simply vastly underestimating the number of dependencies and their criticality to an organization’s operations,” Clements said.
“These third-party tools, by their nature, often require administrative rights to many if not all a customer’s devices that they interact with, meaning a compromise of just one of these vendors may be enough to completely compromise their customer’s environments as well.”
“Similarly, there is often ignorance of just how much many organizations depend on third-party vendors,” he continued, “Most organizations I know don’t have a ready-to-go fallback plan if a major provider such as their email communications platform were to have an extended outage.”
Even in situations where leaders do understand the risks to their supply chain, they won’t err on the side of security. “In situations where companies have to choose between security and growth, every time you will see them choosing growth,” observed Casey Bisson, head of product and developer relations for BluBracket, a cybersecurity services company in Menlo Park, Calif.
“That comes at the risk of their customers. That comes at the risk of the company itself,” he told TechNewsWorld. “But increasingly, we’re starting to see executives being held responsible for those choices.”
The ISACA survey also found a strong vein of pessimism among the IT Pros about the security prospects of their supply chains. Only 44% indicated they have high confidence in the security of their organization’s supply chain, while 53% expect supply chain issues to remain the same or get worse over the next six months.
Source: ISACA | Understanding Supply Chain Security Gaps | 2022 Global Research Report
One of the more surprising findings of the survey was that 25% of the organizations said they’d experienced a supply chain attack in the last 12 months. “I did not think it would be anywhere near that high,” Clyde said.
“While many organizations have experienced cyberattacks in the last 12 months, I didn’t think there would be this many attributing it to a supply chain problem. If we asked that question several years ago, that would have been a very low number,” he added.
Meanwhile, more than eight out of 10 of the tech experts (84%) said their supply chains needed better governance than what they have now.
“The way we try to certify supply chain partners today just doesn’t work,” maintained Andrew Hay, COO of Lares, an information security consulting firm in Denver.
“We either generate an arbitrary score based on external scan data and IP-based confidence or we try and force them to fill out 100 or more questions on a spreadsheet,” he told TechNewsWorld. “Neither accurately depicts how secure an organization is.”
Mike Parkin, a senior technical engineer with Vulcan Cyber, a provider of SaaS for enterprise cyber risk remediation in Tel Aviv, Israel, noted that there are multiple factors that come into play when trying to secure the supply chain.
“Organizations only ever have full visibility into their own environment, which means they have to trust their vendors are following best practices,” he told TechNewsWorld. “This means they need to include contingencies for when a third-party vendor is breached or build a process that severely restricts the damage that can occur if it does happen.”
“That’s even more complicated when an organization needs to deal with multiple vendors to compensate for shortages or disruptions,” he continued. “Even with the correct risk management tools, it can be hard to account for everything in play.”
Kron added that there has to be some trust in suppliers; however, if governance is increased to confirm what organizations tell us, as opposed to just trusting answers from a questionnaire, a system of auditing has to be put in place.
“This will inevitably increase costs, something that many organizations work hard to keep as low as possible in order to remain competitive,” he said.
“While this may be easier to justify for critical government or military systems, it can be a tough sell for traditional suppliers,” he maintained. “To add to the challenges, enforcing governance on foreign suppliers of goods and materials may be difficult or impossible to achieve. This is not an easy challenge to tackle and will continue to be a topic of discussion for quite some time.”
John P. Mello Jr. has been an ECT News Network reporter since 2003. His areas of focus include cybersecurity, IT issues, privacy, e-commerce, social media, artificial intelligence, big data and consumer electronics. He has written and edited for numerous publications, including the Boston Business Journal, the Boston Phoenix, Megapixel.Net and Government Security News. Email John.
Please sign in to post or reply to a comment. New users create a free account.
Africa
Asia-Pacific
Eastern Europe
Europe
Latin America
Middle East
North America
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/04/canonical-ubuntu-jammy-jellyfish-300×155.jpg
https://www.technewsworld.com/story/canonical-lets-loose-ubuntu-22-04-lts-jammy-jellyfish-176515.html
Canonical Lets Loose Ubuntu 22.04 LTS ‘Jammy Jellyfish’
Low-Code Platforms Help Ease the Shadow IT Adversity Pain
SaaS Boom Puts Software Sellers on Road to Recurring Revenue
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/webex-room-bar-300×156.jpg
https://www.technewsworld.com/story/new-cisco-conferencing-devices-designed-to-heal-meeting-fatigue-176767.html
New Cisco Conferencing Devices Designed To Heal Meeting Fatigue
Amazon Puts High-Tech Spin on Play Dates With Kiddie Video-Calling Device
4 Industries on the Brink of Technological Disruption
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/satya-nadella-build-2022-300×156.jpg
https://www.technewsworld.com/story/microsofts-innovative-4-processor-pc-176789.html
Microsoft’s Innovative 4-Processor PC
Intel Releases Arc, Now We Have a Three-Horse Race
Apple Refreshes iPhone SE, iPad Air, Debuts Studio Desktop
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/06/canonical-ubuntu-300×156.jpg
https://www.technewsworld.com/story/ubuntu-core-22-release-addresses-challenges-of-iot-edge-computing-176583.html
Ubuntu Core 22 Release Addresses Challenges of IoT, Edge Computing
Titan Linux Beta Brings Simplicity, Finesse to KDE Remake
Don’t Become a Fool in the IT Gold Rush
https://www.technewsworld.com/wp-content/uploads/sites/3/2021/08/power-grid-300×156.jpg
https://www.technewsworld.com/story/cloudflare-cloudstrike-ping-identity-offer-free-services-to-protect-us-critical-infrastructure-87440.html
Cloudflare, CloudStrike, Ping Identity Offer Free Services To Protect US Critical Infrastructure
CyberSec Firms Give Advice, Services To Quell Fallout From Malware Aimed at Ukraine
Russia-Linked Cyclops Blink Malware Identified as Potential Cyberwarfare Weapon
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/sysadmin-data-300×156.jpg
https://www.technewsworld.com/story/data-observabilitys-big-challenge-build-trust-at-scale-176667.html
Data Observability’s Big Challenge: Build Trust at Scale
The Business Case for Clean Data and Governance Planning
6 Critical Steps for Scaling Secure Universal Data Authorization
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/06/hp-dev-one-pop-os-300×156.jpg
https://www.technewsworld.com/story/new-linux-laptop-line-advances-hp-system76-open-source-collaboration-176562.html
New Linux Laptop Line Advances HP, System76 Open-Source Collaboration
Open-Source Code a Marginal Problem, Managing It the Key Challenge: Report
Appdome CEO on Mobile App Security: No Developer, No Code, No Problem
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/06/crypto-wallet-300×156.jpg
https://www.technewsworld.com/story/cryptocurrency-custody-concerns-who-holds-the-digital-storage-keys-176683.html
Cryptocurrency Custody Concerns: Who Holds the Digital Storage Keys?
The 5 Coolest Things at Dell World Almost No One Saw
Meta vs. Varjo and Nvidia: The Bifurcation of the Metaverse
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/sports-betting-apps-300×156.jpg
https://www.technewsworld.com/story/sports-betting-platforms-gambling-with-substandard-cx-176483.html
Sports Betting Platforms Gambling With Substandard CX
Natural Language Speaks Loudly About a Big Shift in AI
Gamifying EdTech Launches Learning to Loftier Levels
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/03/nvidia-gtc-22-300×156.jpg
https://www.technewsworld.com/story/nvidia-showcases-the-metaverse-future-at-gtc-87465.html
Nvidia Showcases the Metaverse Future at GTC
Play-To-Earn Gaming Faces Hurdles To Rapid Growth
The Coolest Stuff From CES 2022
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/data-leak-300×156.jpg
https://www.technewsworld.com/story/ransomware-related-data-leaks-jump-82-in-2021-87419.html
Ransomware-Related Data Leaks Jump 82% in 2021
49ers Blitzed by Ransomware
Reports Warn of Worsening Warfare From Cyber Criminals in 2022
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/innoview-pm004-300×156.jpg
https://www.technewsworld.com/story/innoviews-15-6-4k-portable-panel-could-be-the-ultimate-touchscreen-accessory-176726.html
InnoView’s 15.6″ 4K Portable Panel Could Be the Ultimate Touchscreen Accessory
InnoView 15.8″ Portable Display: More Screen Space for Small Devices
Tech Industry Changes and the Emergence of a World IT Army
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/lumen-300×156.jpg
https://www.technewsworld.com/story/hack-your-metabolism-to-improve-health-with-the-lumen-smart-device-87350.html
Hack Your Metabolism To Improve Health With the Lumen Smart Device
Amazon Rolls Out Alexa for Senior Living and Healthcare Providers
Cove High-Tech Neckband Aims To Ease Stress, Improve Sleep
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/smart-home-controls-300×156.jpg
https://www.technewsworld.com/story/home-automation-faces-3-perpetual-problems-176684.html
Home Automation Faces 3 Perpetual Problems
How the War in Ukraine Is Changing the Technology Landscape
CES 2022 Predictions
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/04/code-tux-300×156.jpg
https://www.technewsworld.com/story/start-here-when-things-go-wrong-on-your-linux-system-176520.html
Start Here When Things Go Wrong on Your Linux System
Computers Use Processes, So Should You
NICE Platform Answers Call for Hyper-Personal CX Tools
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/03/teamwork-300×156.jpg
https://www.technewsworld.com/story/foundries-and-arduino-team-to-patch-iot-devices-87464.html
Foundries and Arduino Team To Patch IoT Devices
Remote Work Heightens Privacy and Security Anxiety Among Employees
Amazon Super Smart Fridge Is Reportedly in the Works
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/open-source-building-300×156.jpg
https://www.technewsworld.com/story/open-source-leaders-push-wh-for-security-action-176531.html
Open Source Leaders Push WH for Security Action
Ukrainian IT Firm Counterattacks Russian War Lies
US Tech Market Leadership at a Crossroads
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/Log4j-300×156.jpg
https://www.technewsworld.com/story/deadly-log4j-hole-expands-victim-vulnerability-87373.html
Deadly Log4j Hole Expands Victim Vulnerability
Researchers Track Linux Intrusions to Cryptojacking Gang
Outlaw Installer for Windows 11 Infected With Malware
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/boy-screen-time-300×156.jpg
https://www.technewsworld.com/story/kids-screen-use-sees-fastest-rise-in-4-years-176735.html
Kids’ Screen Use Sees Fastest Rise in 4 Years
What’s in Store for Next-Gen Digital Wallets
Apple Privacy Rule Cost Tech Titans Estimated $9.85 Billion in Revenue
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/computer-user-300×156.jpg
https://www.technewsworld.com/story/new-breeze-theme-gives-kde-neon-release-lots-of-sparkle-87388.html
New Breeze Theme Gives KDE Neon Release Lots of Sparkle
HP Chromebase Makes Chrome OS Desktops a Smart Choice
Why Microsoft Again Became the World’s Most Valuable Company
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/04/cybercrime-300×156.jpg
https://www.technewsworld.com/story/us-led-seizure-of-raidforums-may-defy-lasting-effect-on-security-176650.html
US-Led Seizure of RaidForums May Defy Lasting Effect on Security
Crypto 101: Data Privacy and Security on Cryptocurrency Platforms
Russian Warpath Prompts Free VPN Offer
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/03/apis-cor-3d-building-300×156.jpg
https://www.technewsworld.com/story/rebuilding-ukraine-3d-printing-and-the-metaverse-could-help-create-the-cities-of-tomorrow-87455.html
Rebuilding Ukraine: 3D Printing and the Metaverse Could Help Create the Cities of Tomorrow
Desklab Portable Monitor: Ideal for Work, Play, Mobile Productivity
Why Commercial Space Travel Is Unlikely To Scale Up
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/frustrated-computer-user-300×156.jpg
https://www.technewsworld.com/story/report-finds-us-workers-lagging-in-digital-skills-87352.html
Report Finds US Workers Lagging in Digital Skills
Nvidia Launches Earth 2 and Goes to War Against Climate Change
The Challenge and Promise of Quantum Computing
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/microsoft-bing-300×156.jpg
https://www.technewsworld.com/story/microsoft-bing-yandex-create-new-search-protocol-87311.html
Microsoft Bing, Yandex Create New Search Protocol
Botify SEO Platform Helps Brands Navigate Organic Search Rankings
Google Cloud Seeks To Cure Retailers’ Search Woes, Help Compete With Amazon
https://www.technewsworld.com/wp-content/uploads/sites/3/2021/08/linux-concept-300×156.jpg
https://www.technewsworld.com/story/30-years-of-linux-history-told-via-distros-87239.html
30 Years of Linux History Told via Distros
Stale Open Source Code Rampant in Commercial Software: Report
The Unforeseen Consequences of Amazon’s Boardroom Switch
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/tesla-phone-300×156.jpg
https://www.technewsworld.com/story/tesla-smartphone-could-be-a-game-changer-87363.html
Tesla Smartphone Could Be a Game Changer
Snapdragon 8 Suggests the End of PCs and Smartphones as We Know Them
Google vs. Apple Smartphones: Similar Capabilities, Polar Opposites in Strategic Execution
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/kyiv-ukraine-300×156.jpg
https://www.technewsworld.com/story/big-tech-firms-move-to-squash-deceptive-info-on-ukraine-crisis-87434.html
Big Tech Firms Move To Squash Deceptive Info on Ukraine Crisis
Facebook Pushes Pause on Instagram for Kids
TikTok Tops YouTube in Watch Time Among Android Users
https://www.technewsworld.com/wp-content/uploads/sites/3/2021/08/satellites-300×156.jpg
https://www.technewsworld.com/story/kuo-predicts-iphone-13-will-support-satellite-calls-and-texting-87255.html
Kuo Predicts ‘iPhone 13’ Will Support Satellite Calls and Texting
30 Years Later, the Trajectory of Linux Is Star Bound
Amazon Clears FCC Hurdle to Satellite Network
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/call-center-team-300×156.jpg
https://www.technewsworld.com/story/marketers-beware-floridas-mini-tcpa-176642.html
Marketers: Beware Florida’s Mini-TCPA
Nasuni Founder Andres Rodriguez: Object Storage Offers More Cloud Benefits, Lower Cost
A Step Into Meta’s VR Meeting World, Horizon Workrooms
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/surface-duo-2-300×156.jpg
https://www.technewsworld.com/story/microsoft-finally-has-truly-competitive-alternatives-to-apple-products-87282.html
Microsoft Finally Has Truly Competitive Alternatives to Apple Products
New iPad Mini Stars at Apple Refresh Event
Chromebook Shipments Jump 75% YoY in Q2
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/04/hostile-takeover-300×156.jpg
https://www.technewsworld.com/story/the-fascinating-dance-between-twitter-and-musk-176654.html
The Fascinating Dance Between Twitter and Musk
Why Pat Gelsinger May Need To Take Intel Private
Reality Check on the Virtual Universe: Metaverse or Metamess?
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/compliance-regulations-300×156.jpg
https://www.technewsworld.com/story/pandemic-compliance-driving-increased-privacy-spending-87331.html
Pandemic, Compliance Driving Increased Privacy Spending
Report Argues Antitrust Bill Would Hurt Consumers, Stymie Innovation
The Rise of Digital Ad Taxes Could Impact Online Marketplaces
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/05/autonomus-vehicles-300×156.jpg
https://www.technewsworld.com/story/blackberry-and-preparing-for-the-software-defined-automobile-176776.html
BlackBerry and Preparing for the Software-Defined Automobile
Wing Picks DFW for First Commercial Drone Deliveries in Major US Metro Area
Advanced Sensor System May Open Door to Zero Death Driving
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/metaverse-shopping-300×156.jpg
https://www.technewsworld.com/story/metaverse-marketing-offers-new-approach-to-utilizing-customer-data-87423.html
Metaverse Marketing Offers New Approach To Utilizing Customer Data
Apple MR Specs Will Shun Metaverse: Report
Apple Wearables Holiday Sales Knock It Out of the Park
https://www.technewsworld.com/wp-content/uploads/sites/3/2022/02/pandemic-holiday-shopping-300×156.jpg
https://www.technewsworld.com/story/5-terrific-tech-gift-ideas-for-your-holiday-shopping-list-87349.html
5 Terrific Tech Gift Ideas for Your Holiday Shopping List
How Qualcomm Can Seize the Smartwatch Market From Apple
Apple Unveils New Muscular MacBooks, Refreshes AirPods, Adds $5 Music Service
https://www.technewsworld.com/wp-content/uploads/sites/3/2021/07/xl-2016-hacker-2-300×184.jpg
https://www.technewsworld.com/story/cybercriminals-employing-specialists-to-maximize-ill-gotten-gains-87200.html
Cybercriminals Employing Specialists To Maximize Ill-Gotten Gains
Encouraging Research Finds Brain Adjusts to ‘Third Thumb’
E-Commerce Tending to Health and Wellness Needs
Copyright 1998-2022 ECT News Network, Inc. All Rights Reserved.
Enter your Username and Password to sign in.
